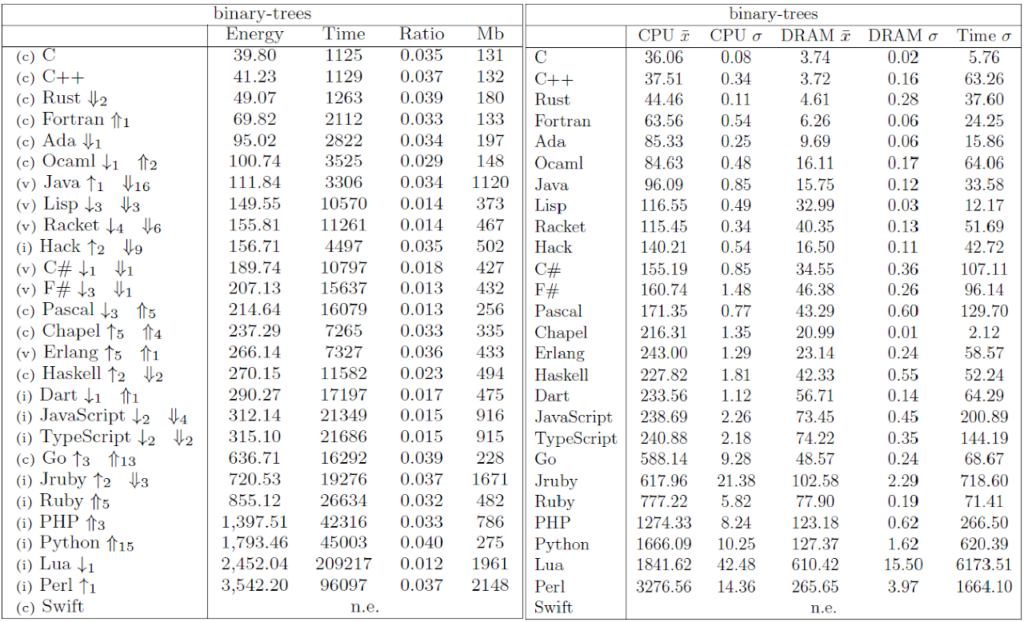
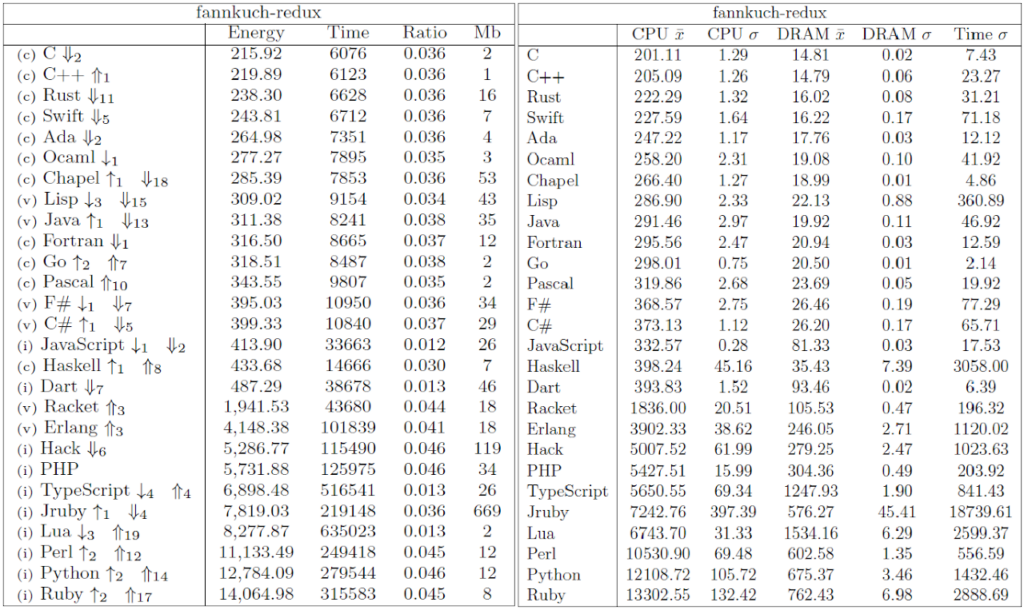
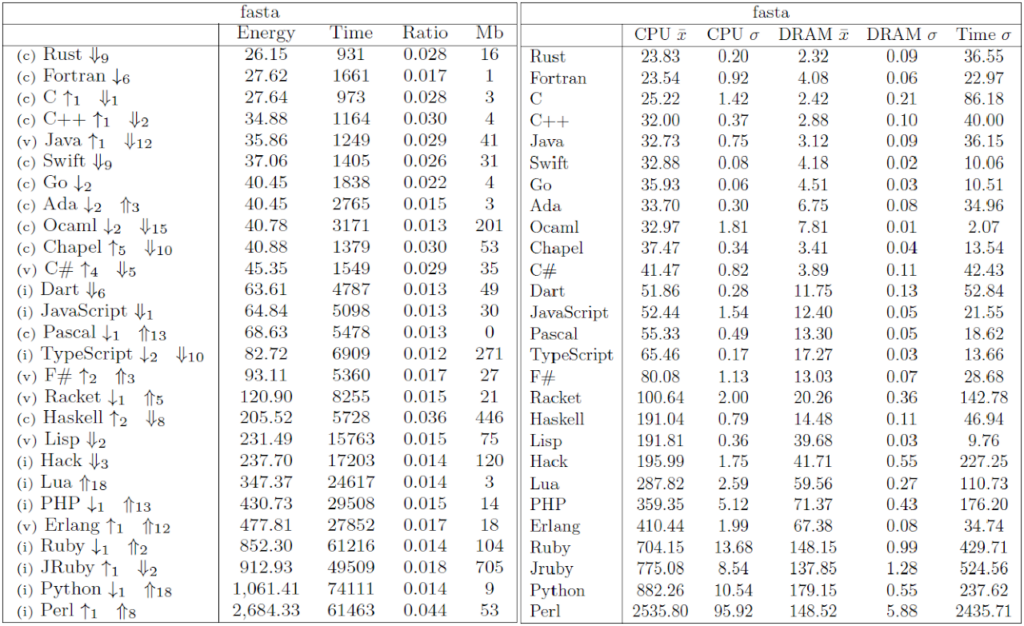
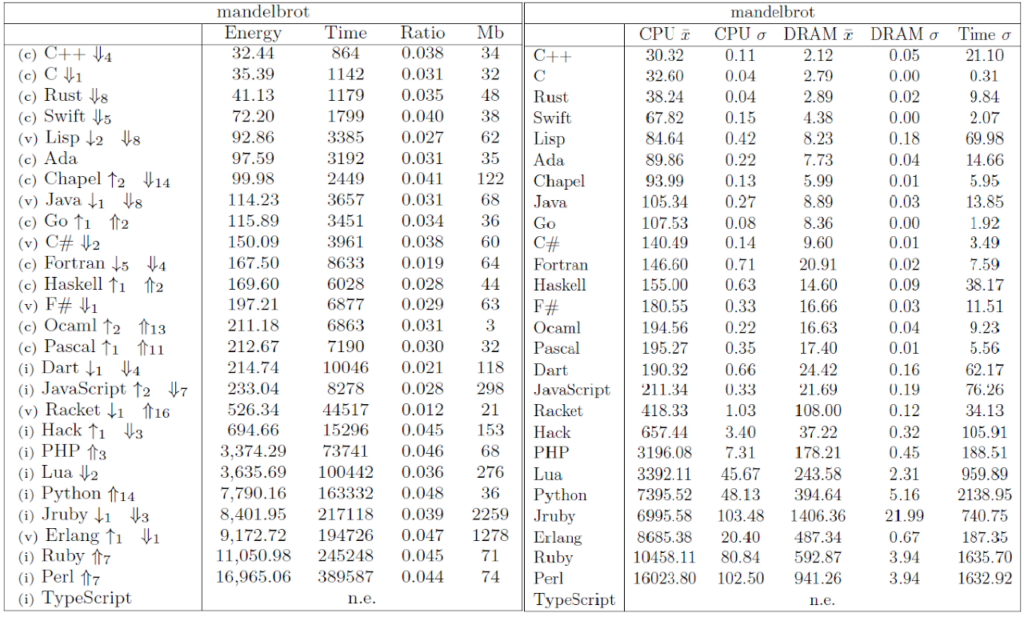
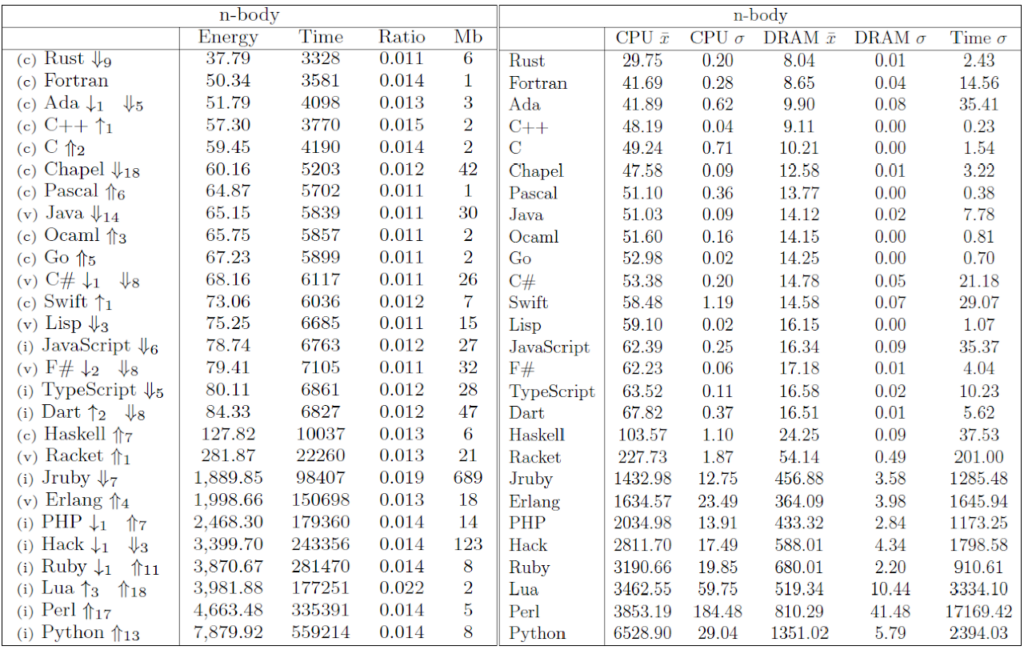
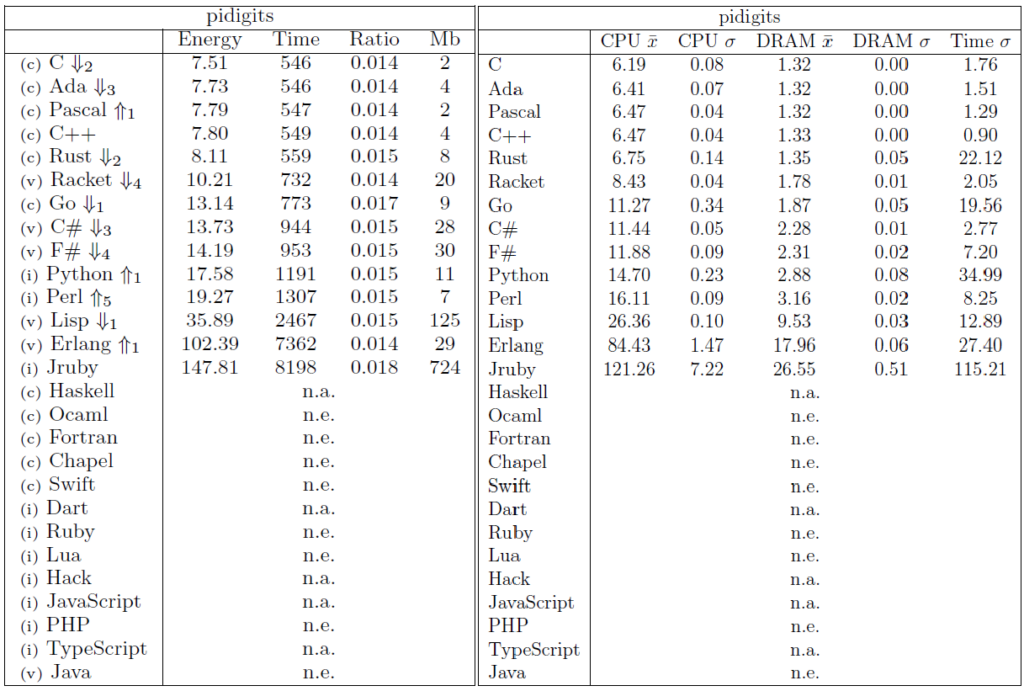
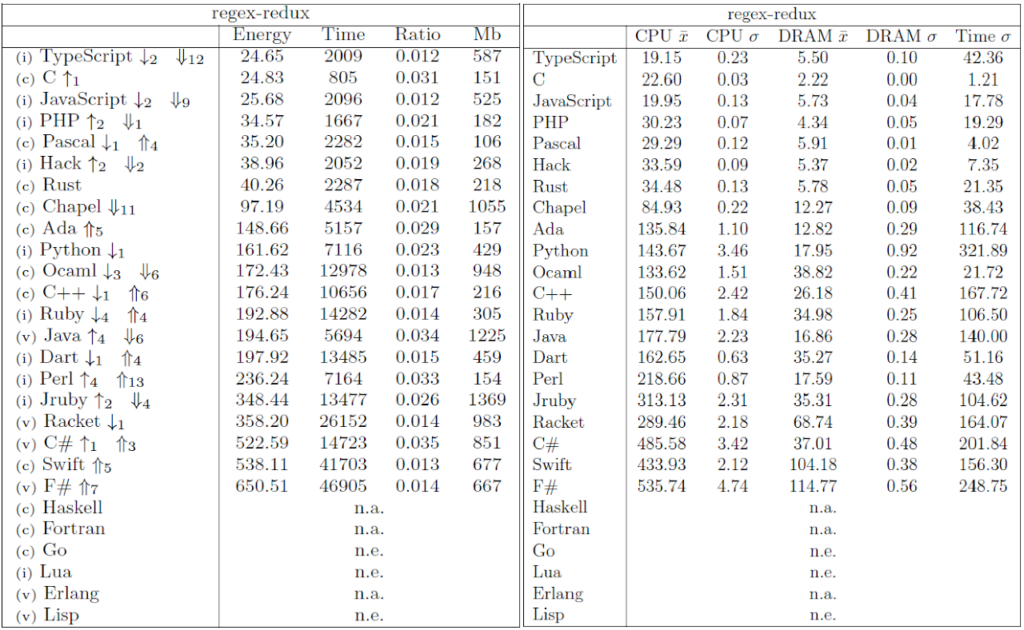
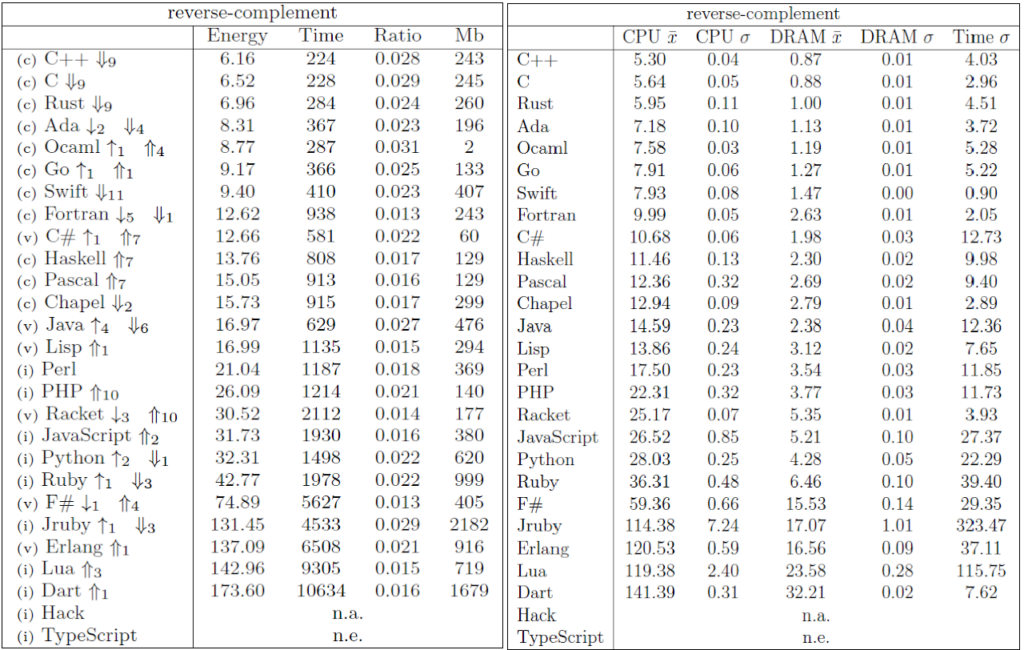
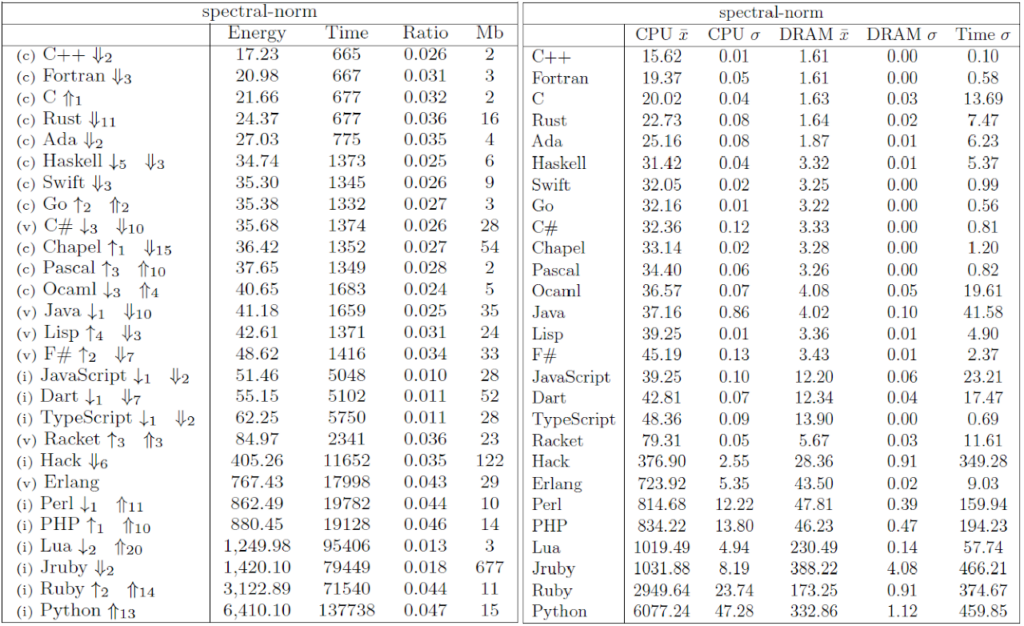
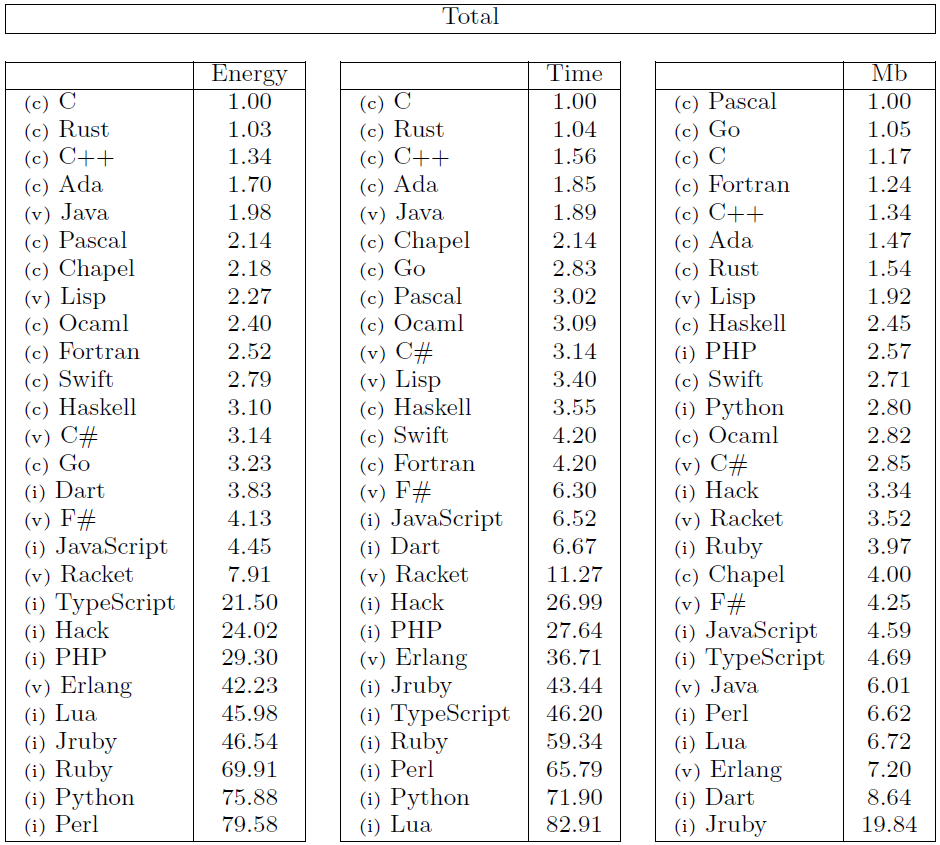
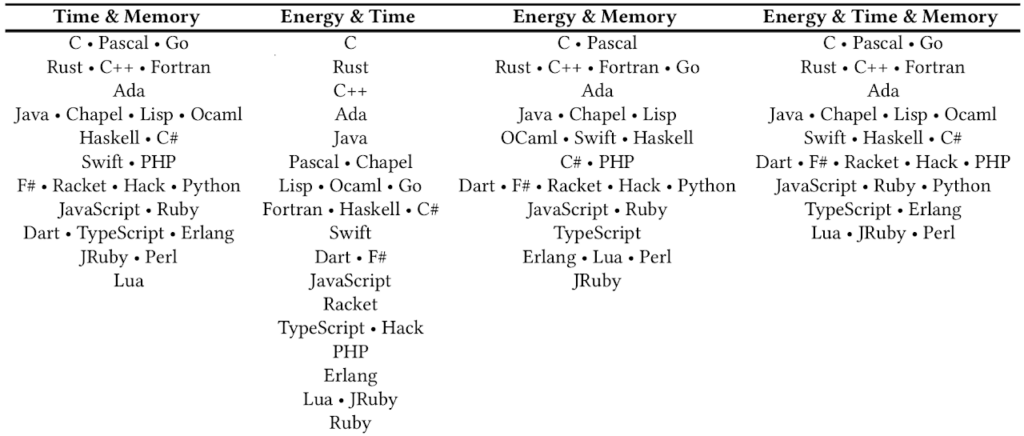
The Computer Language Benchmark Game, also known as “The Benchmarks Game” or previously as “The Great Computer Language Shootout,” is a project that compares the performance of different programming languages using a set of benchmark problems. It’s a valuable resource for researchers comparing language performance.
Here are a few papers from recent years that have utilized CLBG:
- “An Empirical Study on the Energy Consumption of Python Idioms” (2021) by Oliveira et al. This paper used CLBG to study the energy efficiency of different Python programming styles.
- “Performance and Energy Efficiency Across Programming Languages” (2021) by Pereira et al. This study used CLBG to compare the performance and energy consumption of various programming languages.
- “Automated Detection of Performance Regressions Using Statistical Learning Techniques” (2020) by Laaber et al. While not exclusively about CLBG, this paper used it as part of their methodology for detecting performance regressions in software.