Security Infografik
Security Infografik
Sumber:
- https://twitter.com/SecurityGuill
- https://securityguill.com/
- https://twitter.com/SecurityGuill/status/1368241476753371140
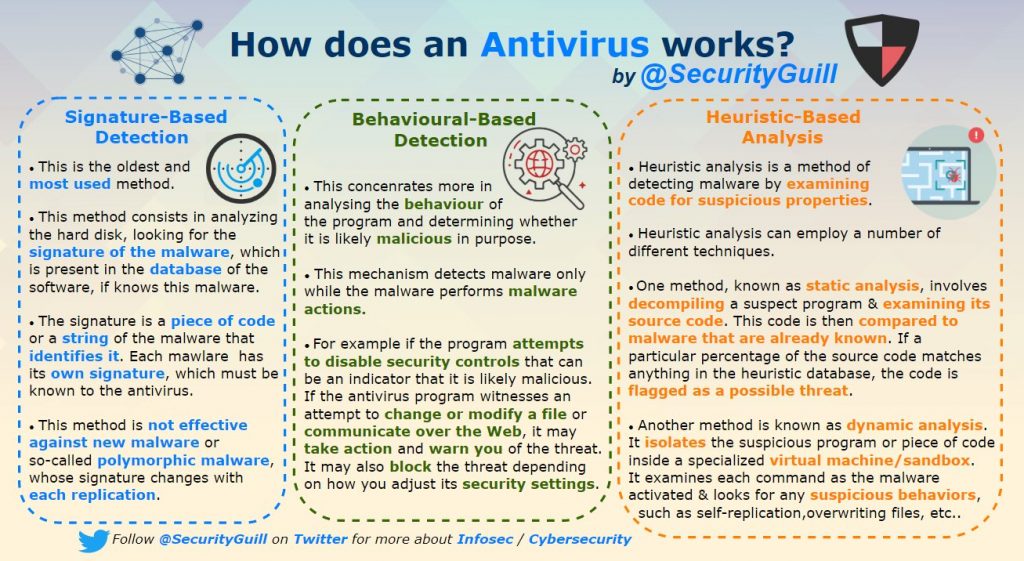
How does an Antivirus works?
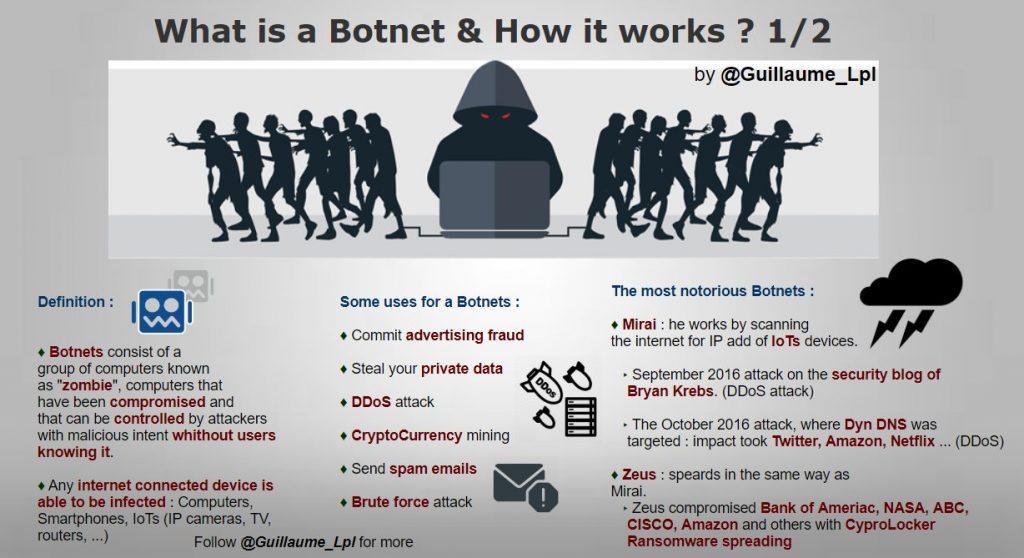
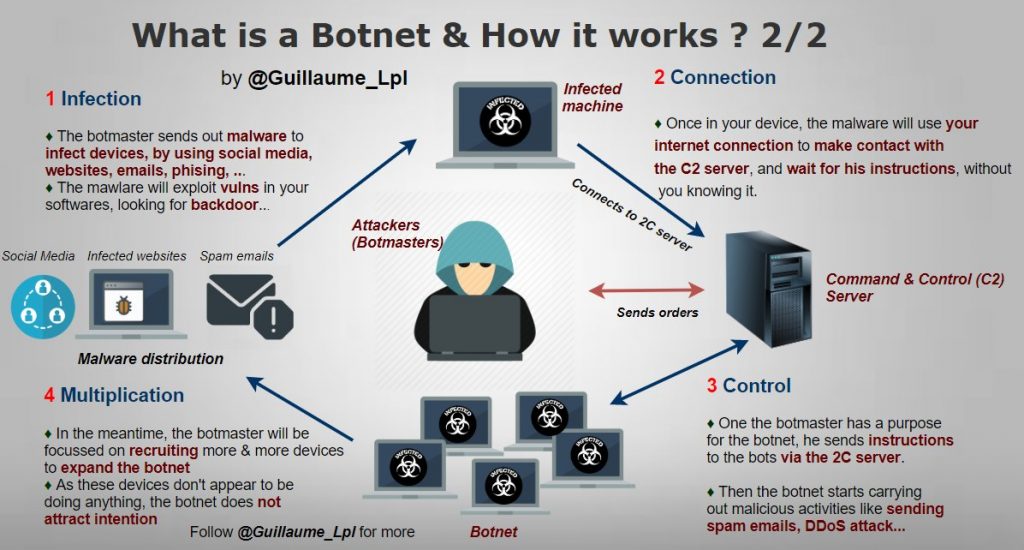
What is a Botnet & How it works
What is a Bug Bounty?

What is a DDos Attack?


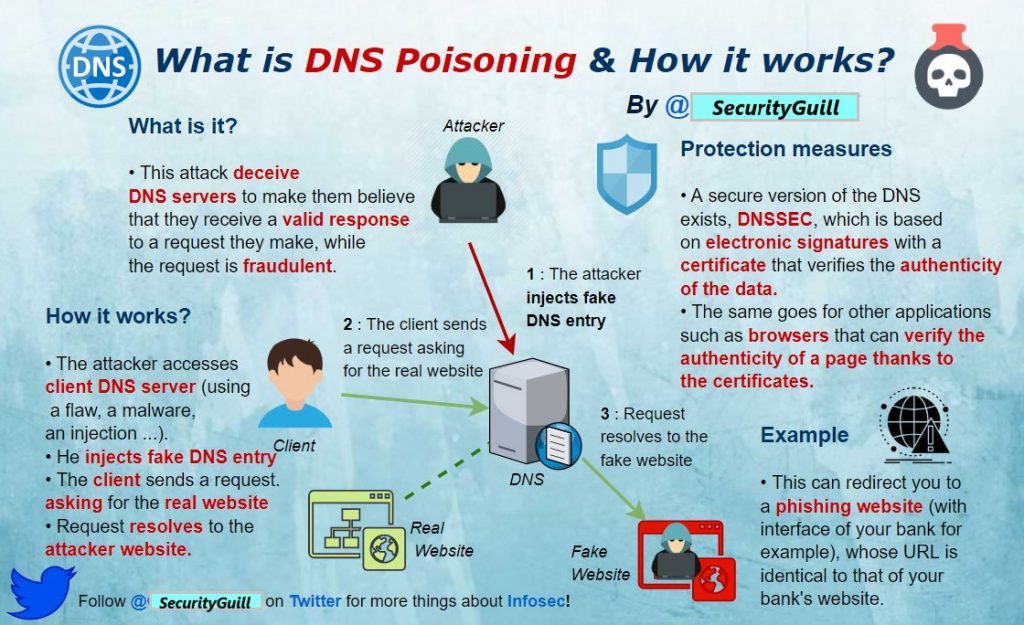
What is DNS Poisoning & How it works?
How End-to-End Encryption Works
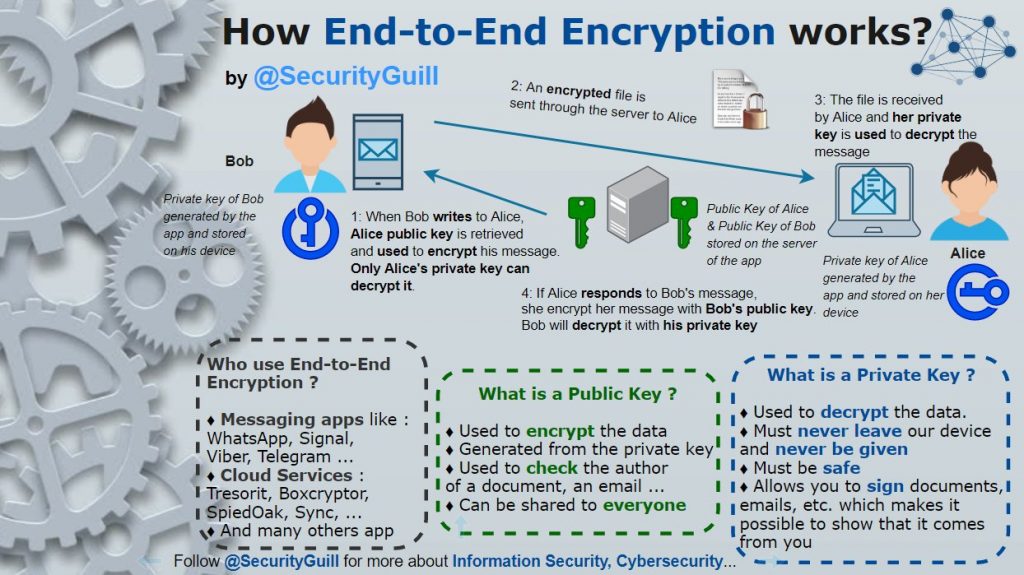
Nine Elements of Digital Forensic Process
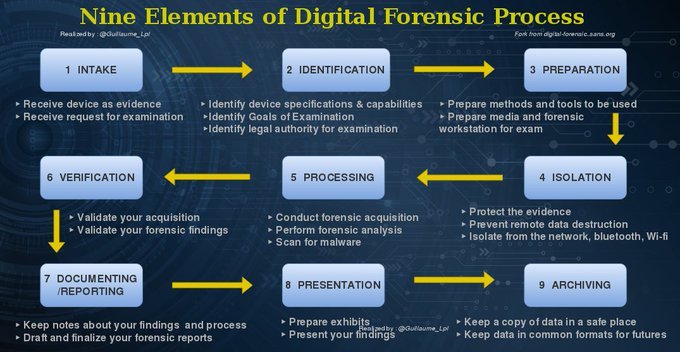
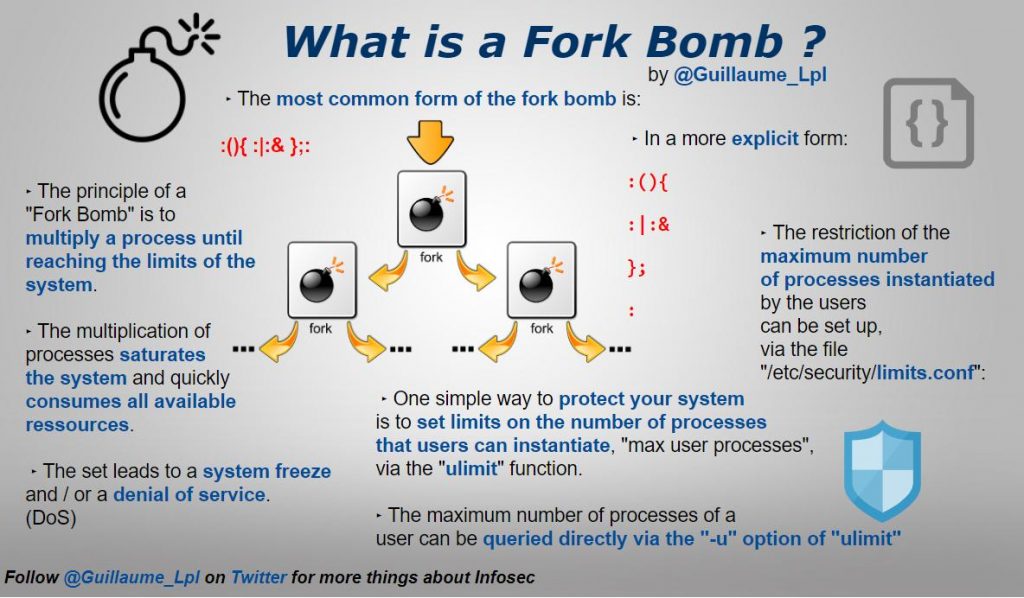
What is a Fork Bomb
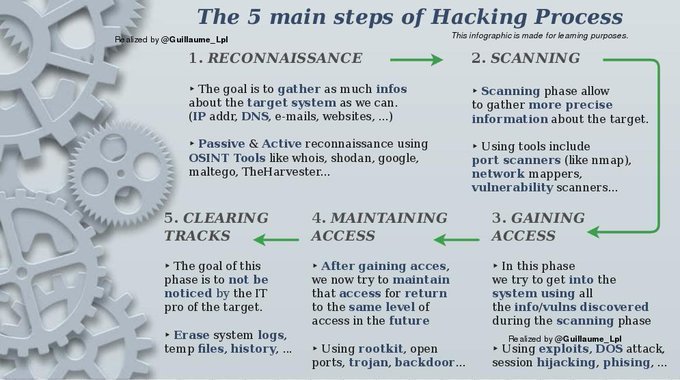
The 5 main steps of Hacking Process
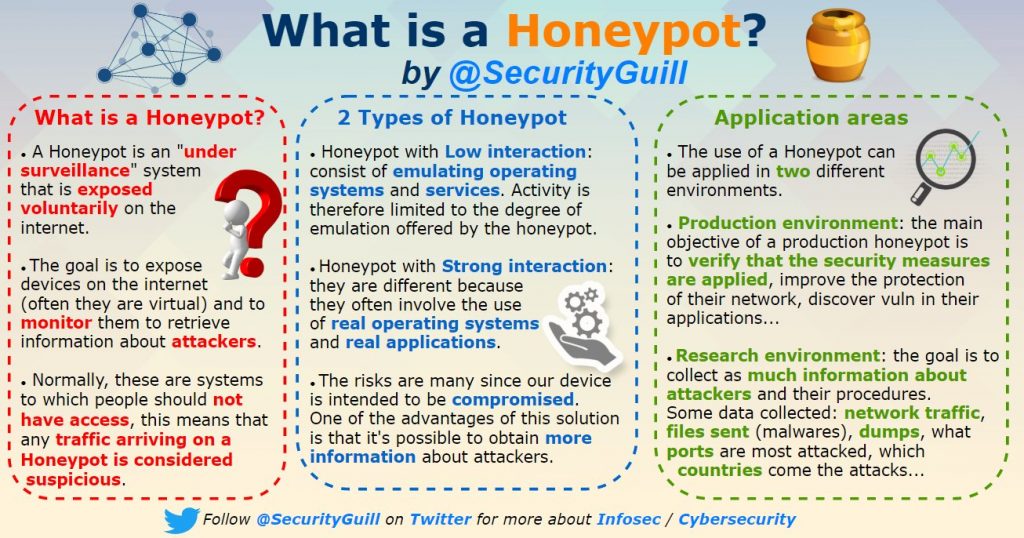
What is a Honeypot
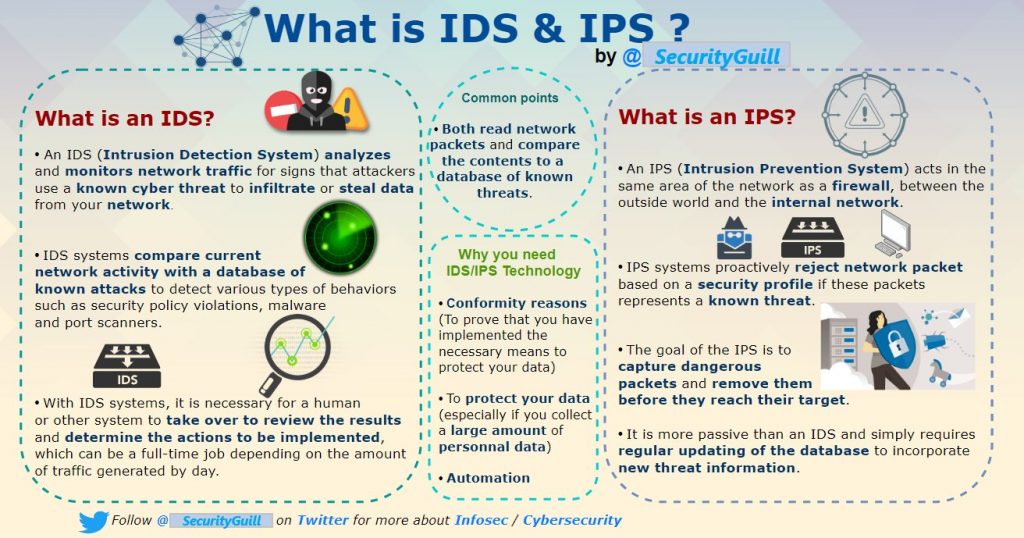
What is IDS & IPS
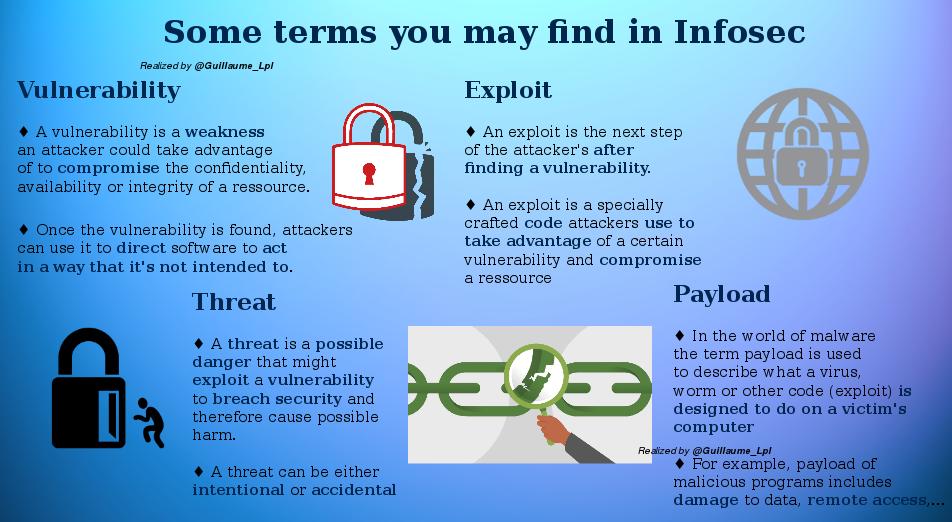
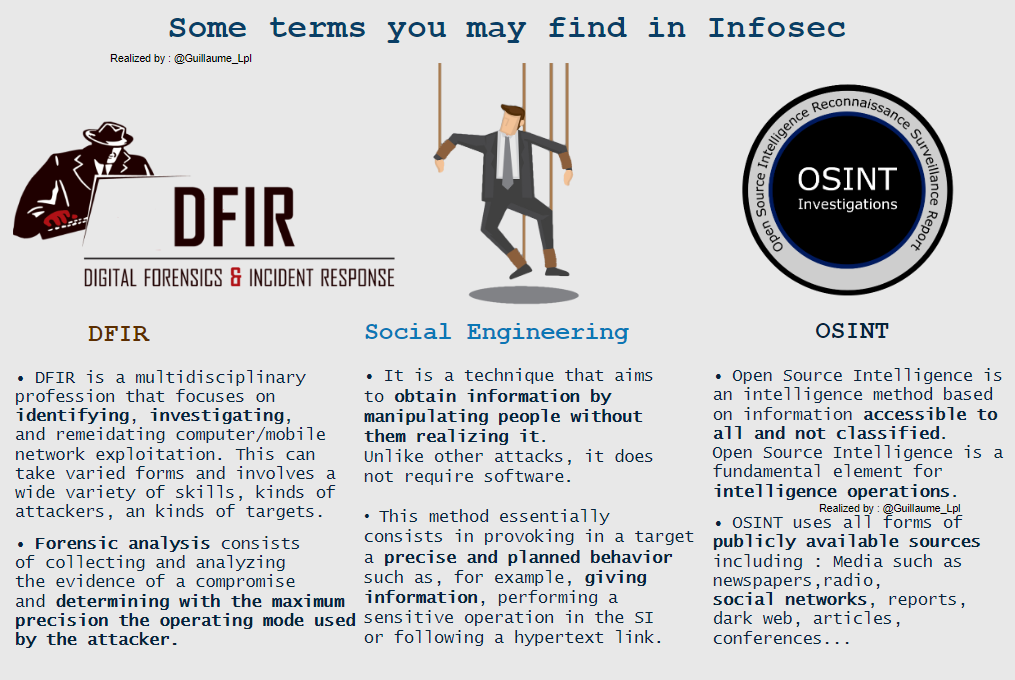
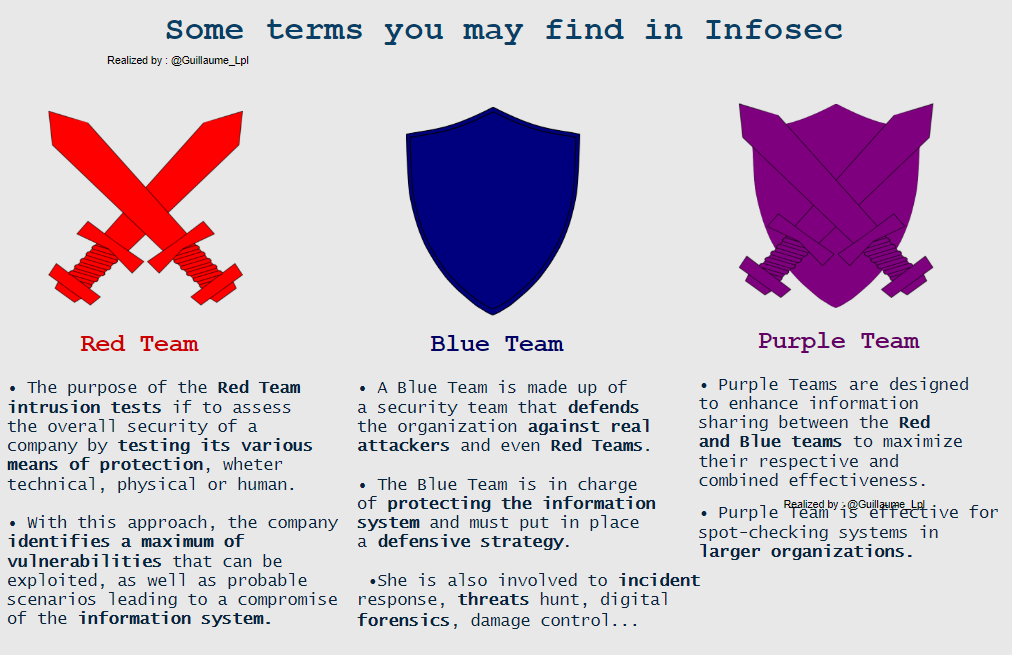
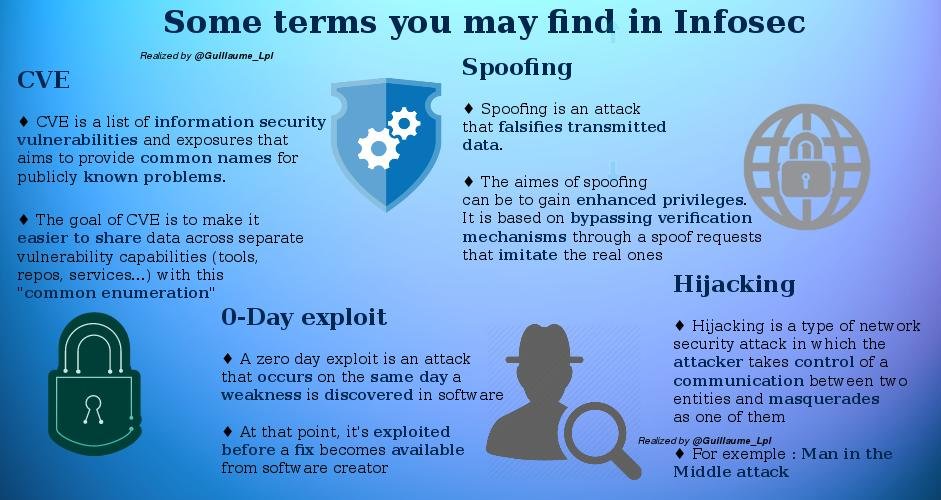
Some infosec Terms
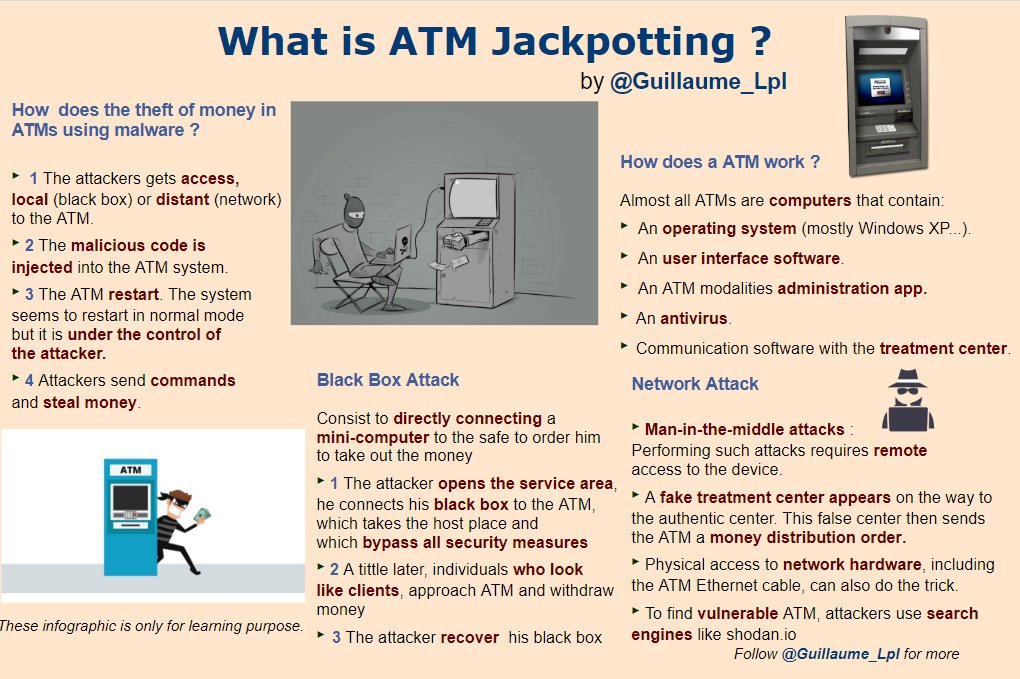
What is Jackpotting
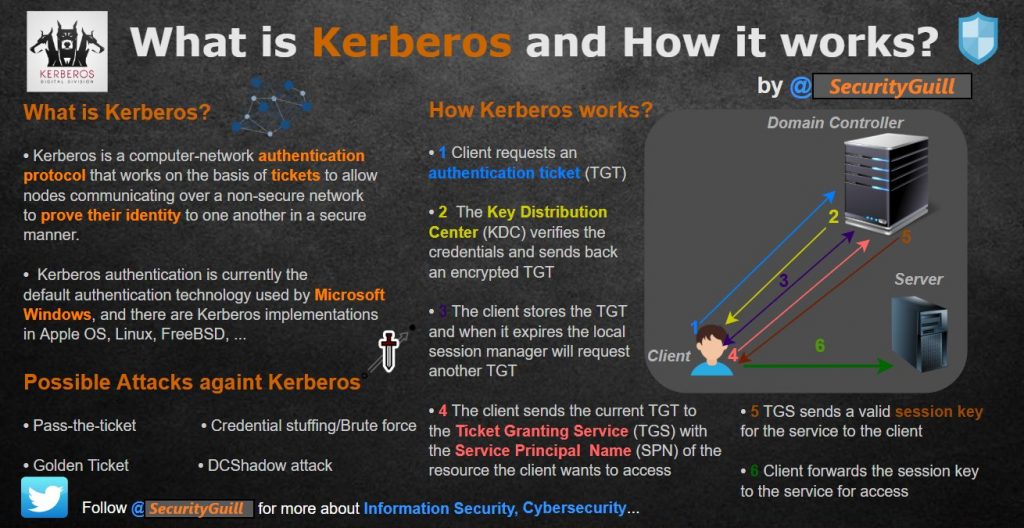
What is Kerberos and How It Works?
What is Kubernetes
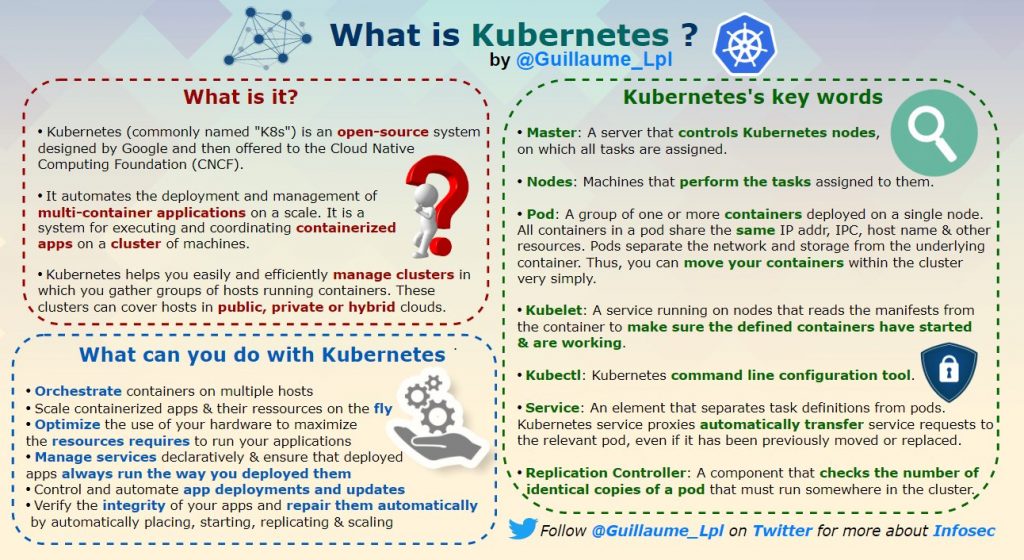
What is LDAP and How It Works?
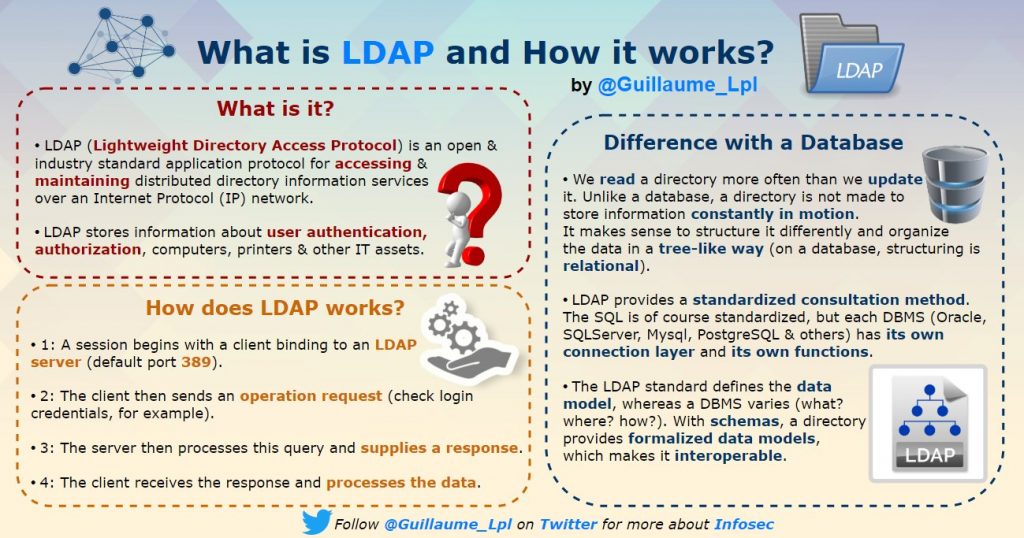
Some Basic Linux COmmands
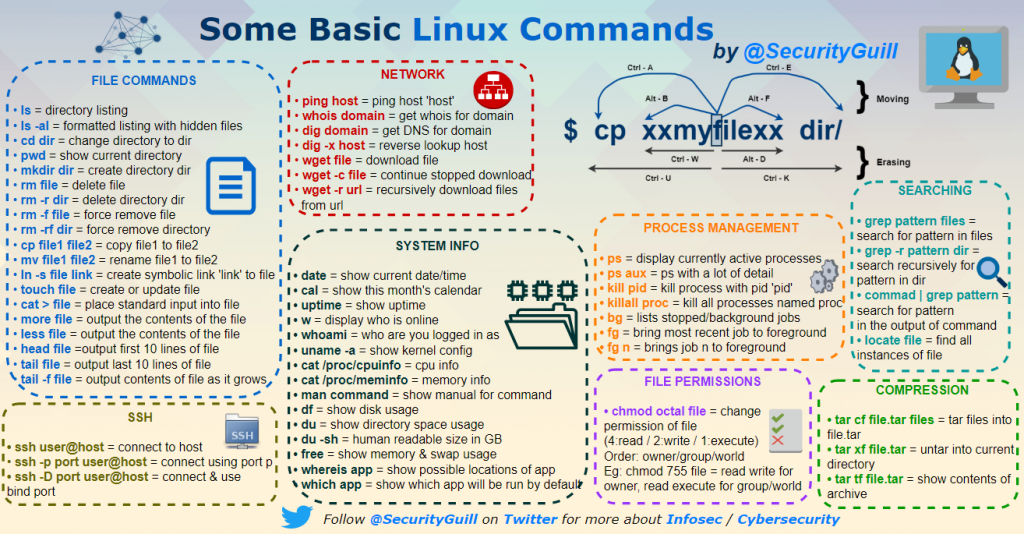
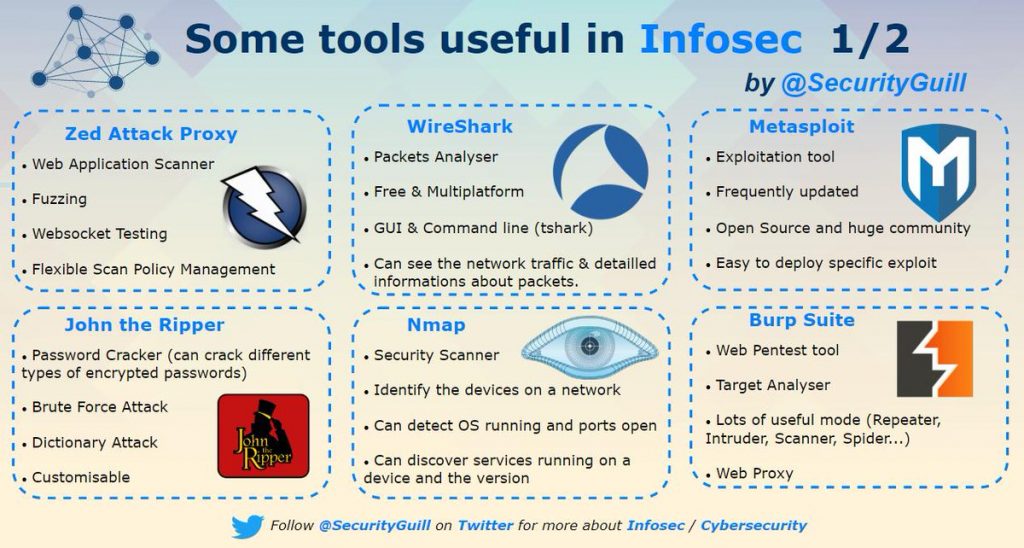
What is Metasploit?
What is MFA
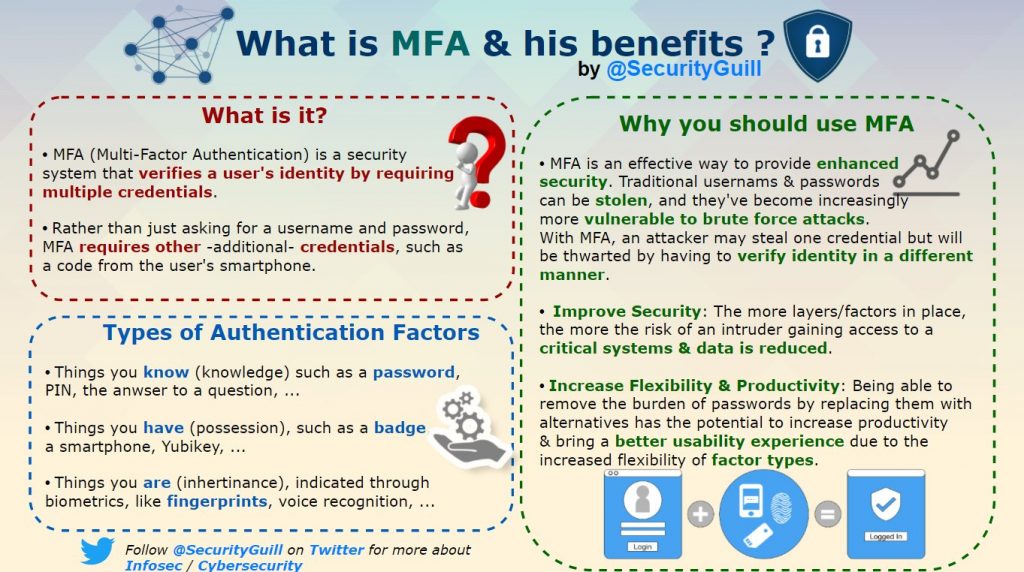
What is Mimikatz?
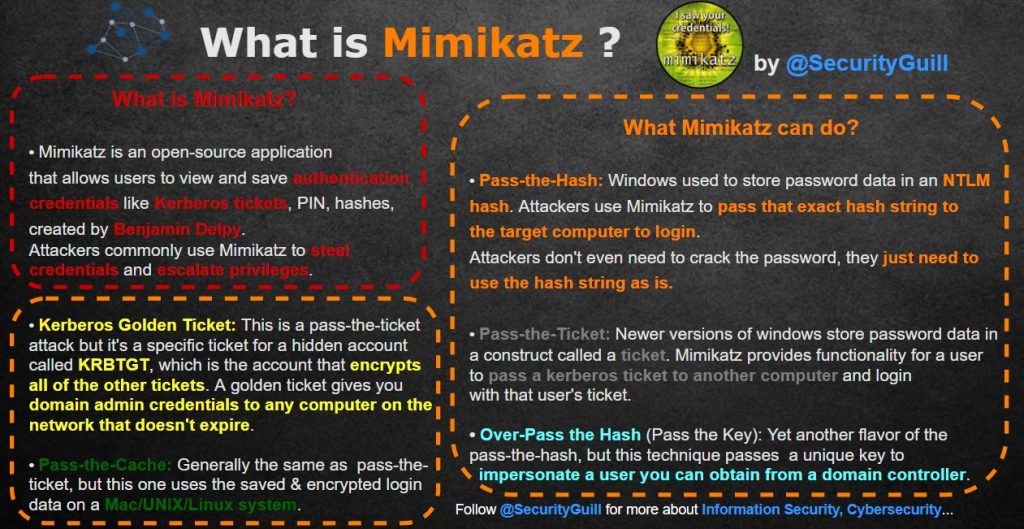
How does Mirai Botnet Works?
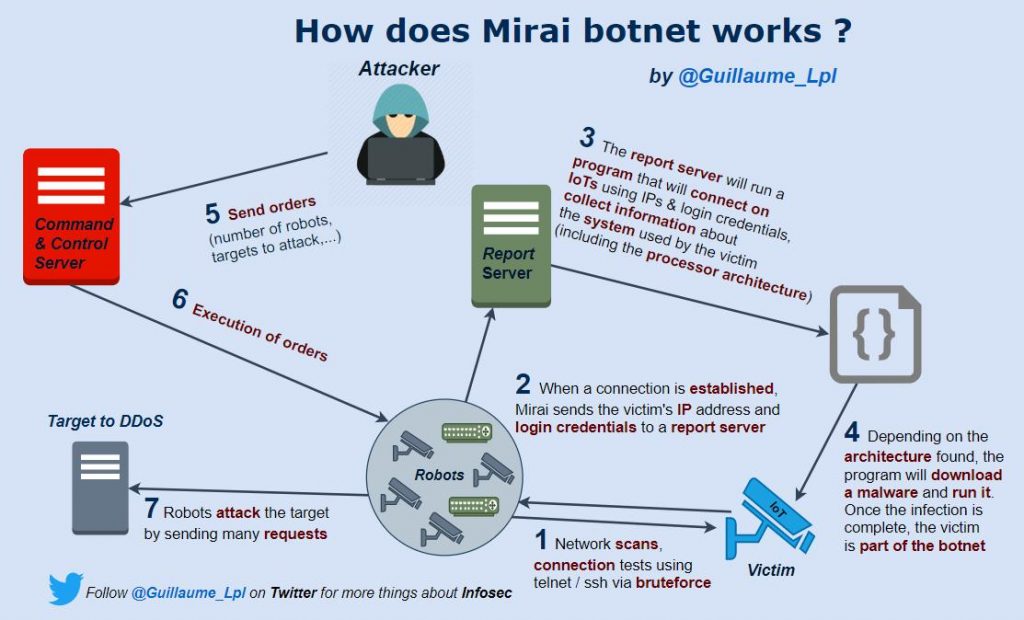
Man in The Middle Attack
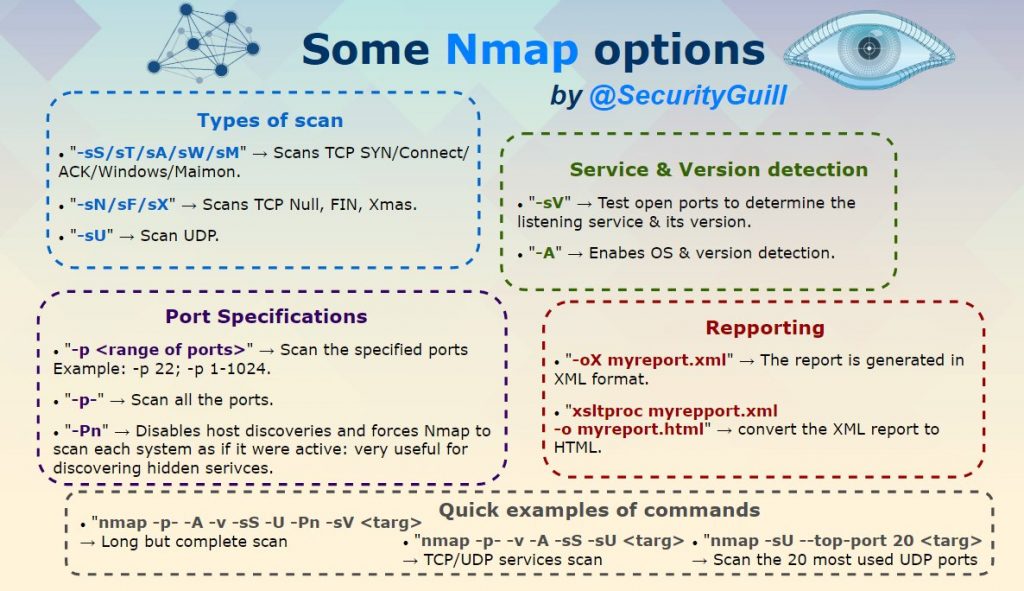
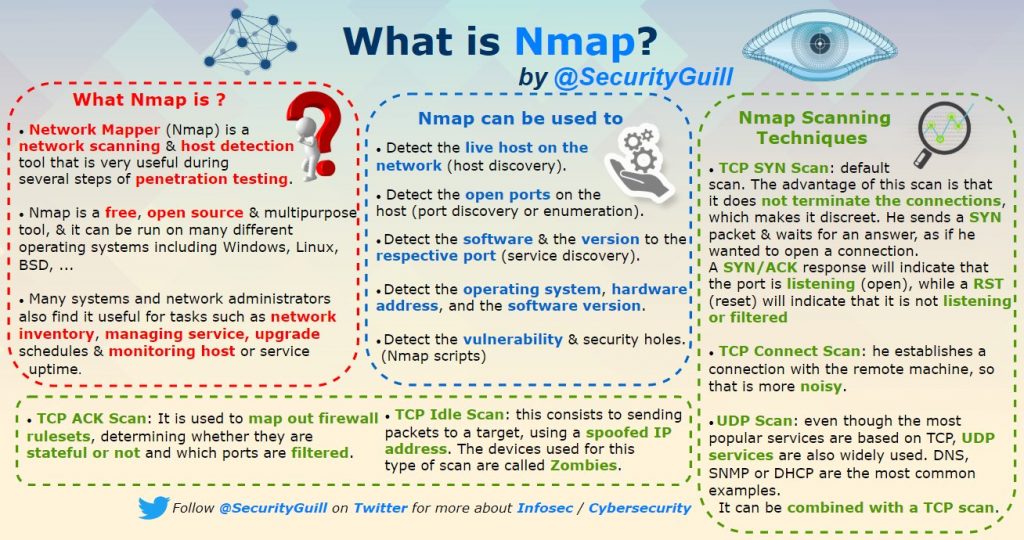
What is Nmap
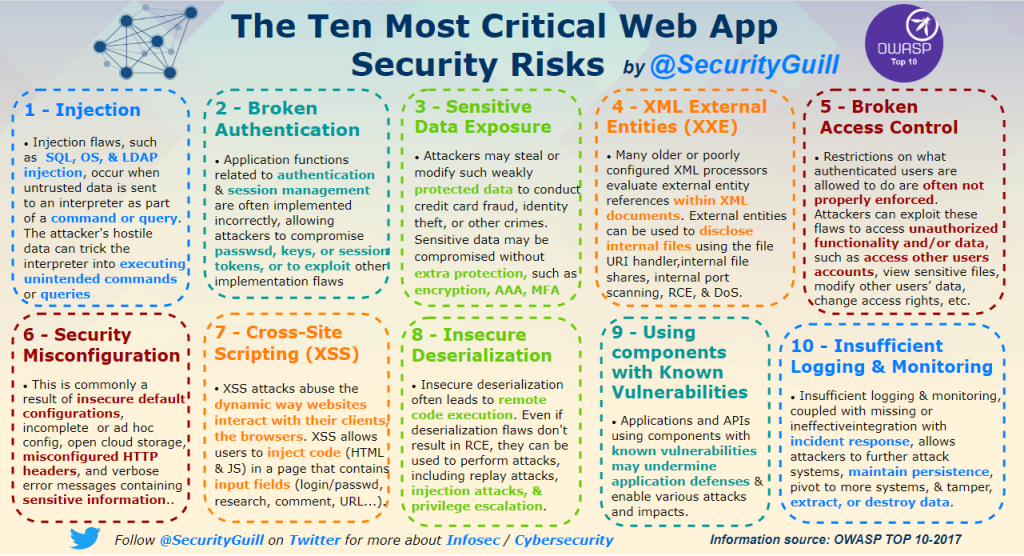
Most Critical Web App Security Risks
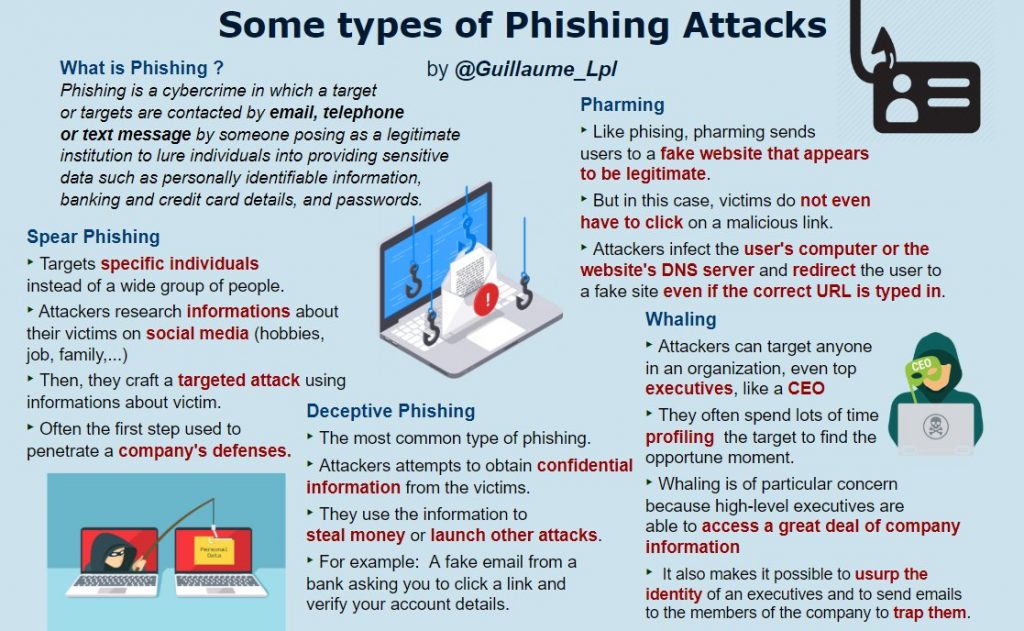
Some types of phishing attacks
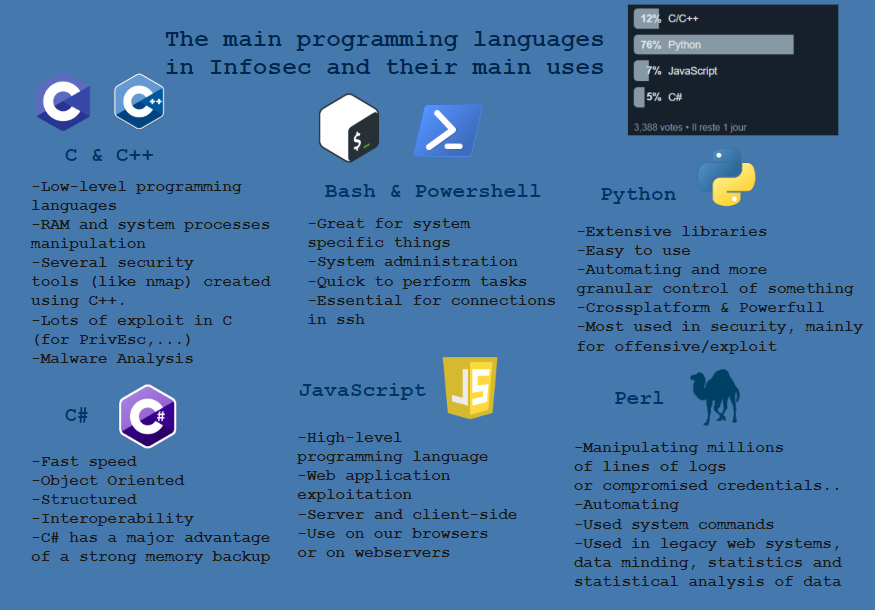
The main programming languges in Infosec and their main uses
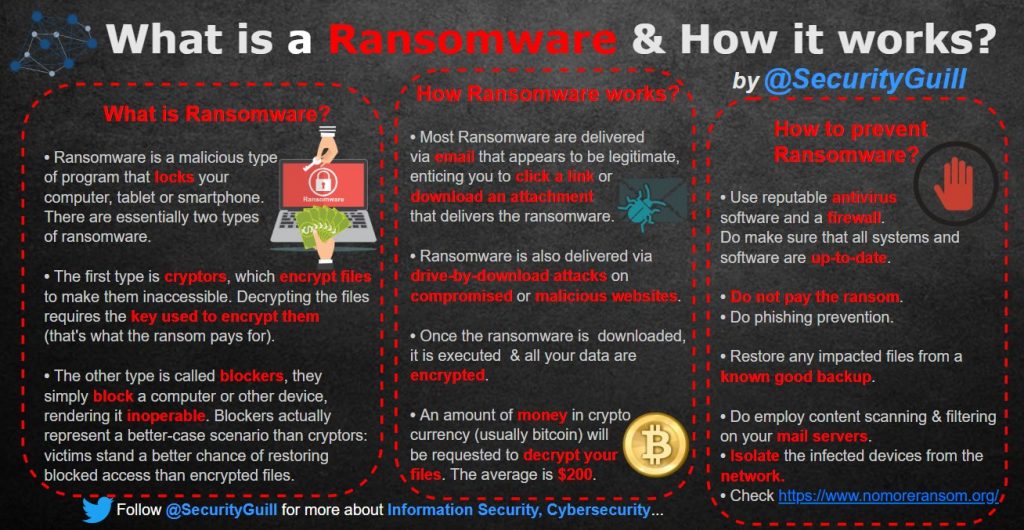
What is ransomware and how it works
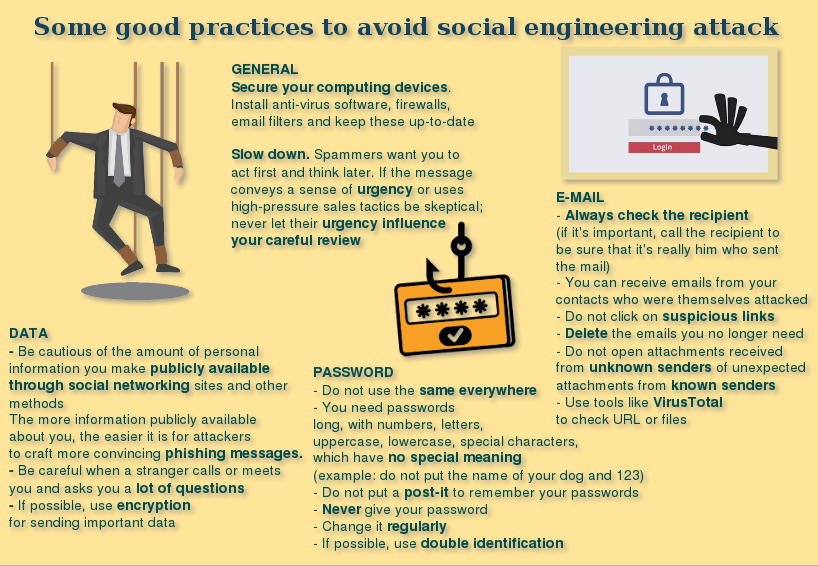
Some good practices to avoid social engineering attack
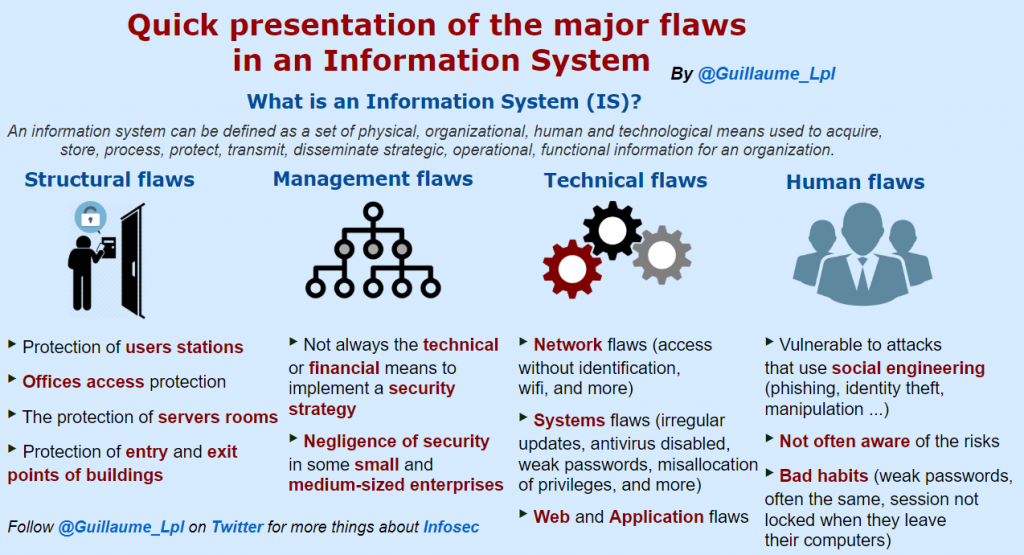
Major flaws in an Information System
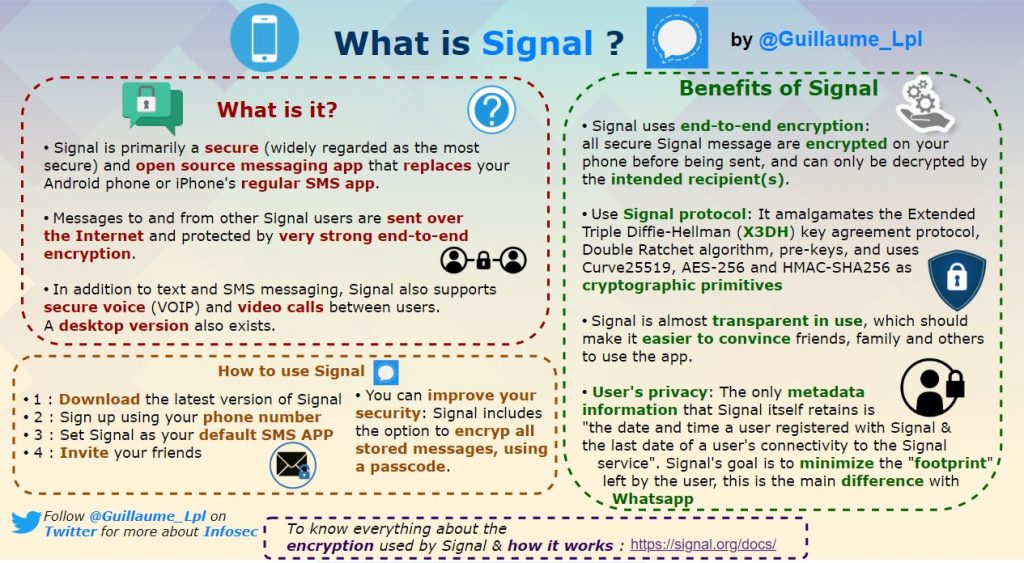
What is Signal
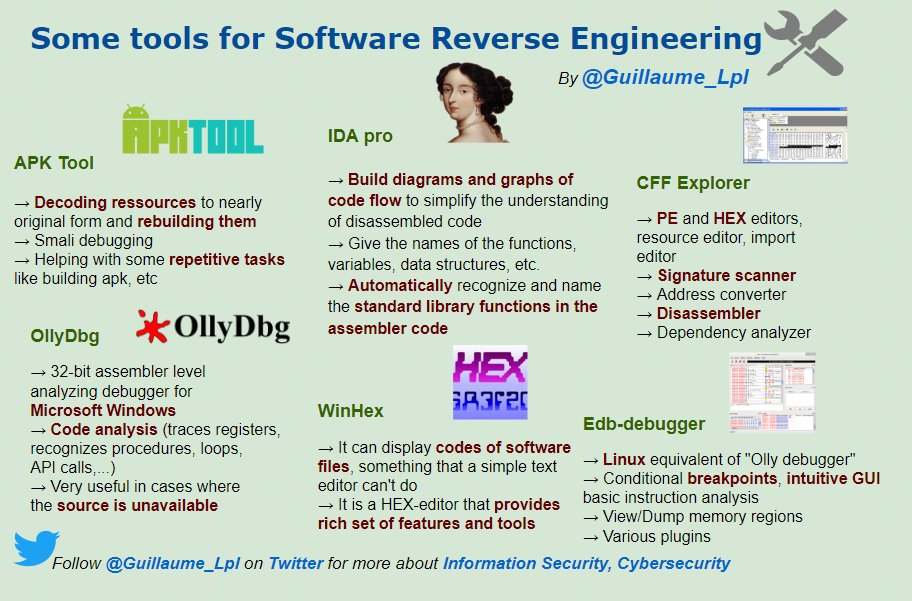
What is Software Reverse Engineering
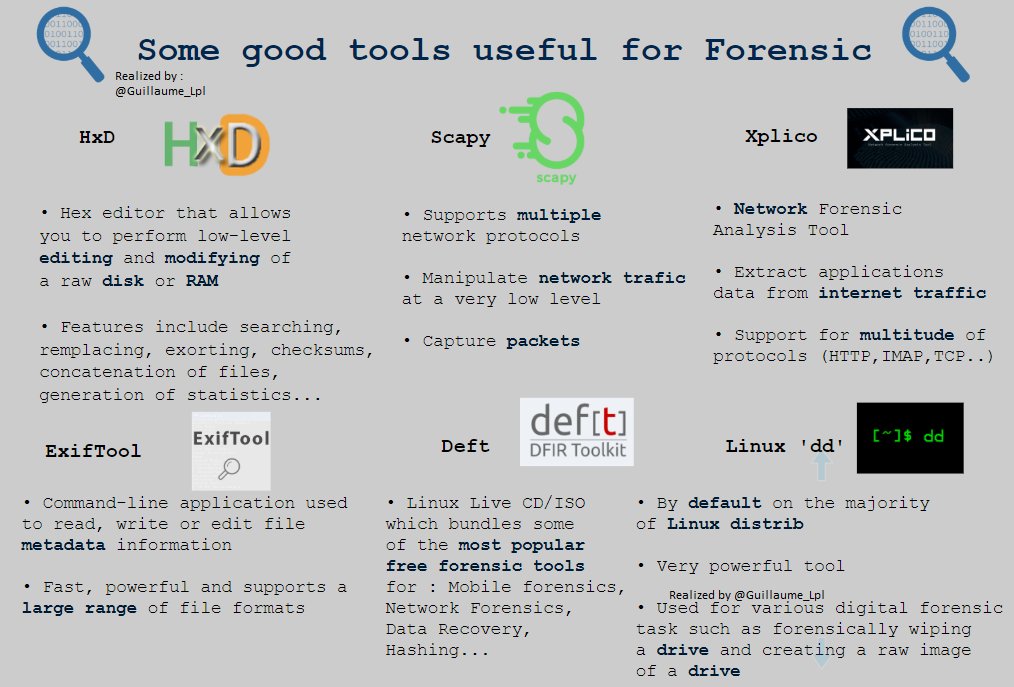
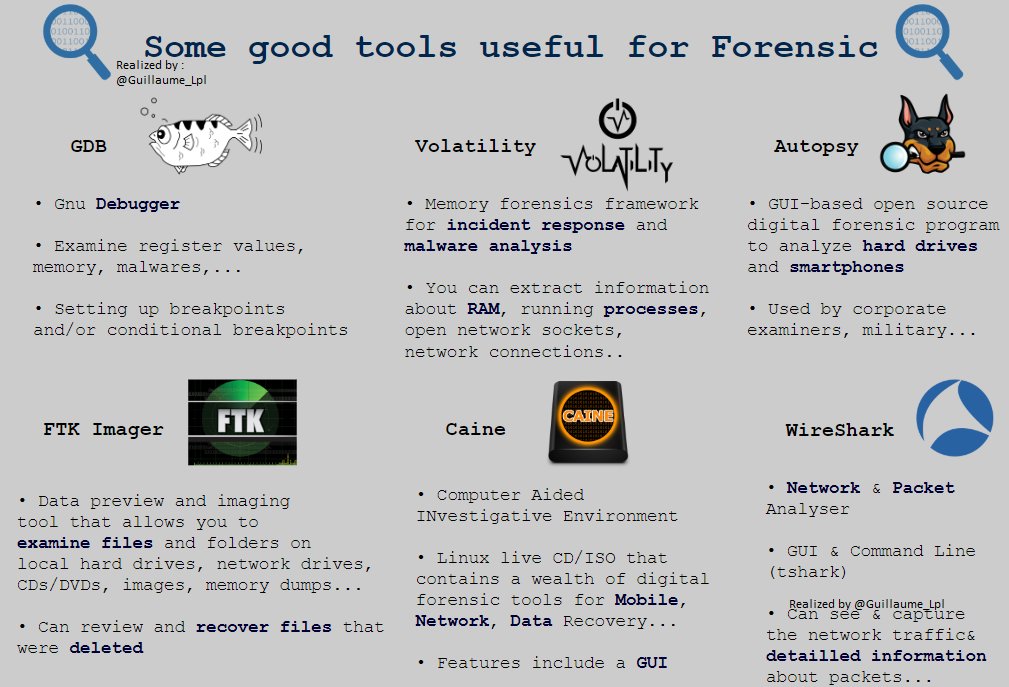
Tools Useful for Forensic Analysis
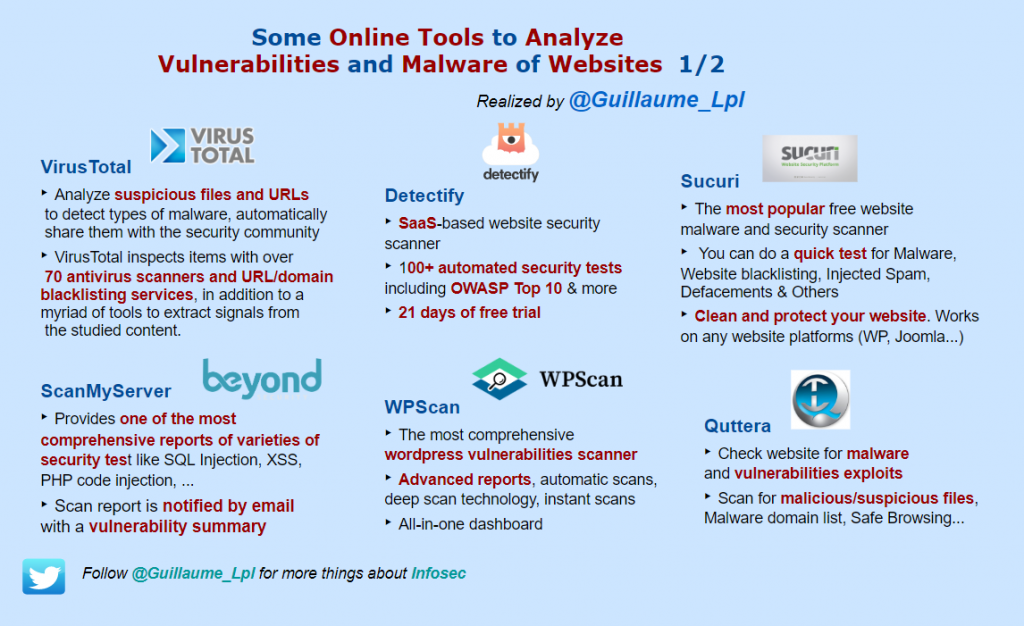
Online Tools to analyze vulnerabilities and malware of websites
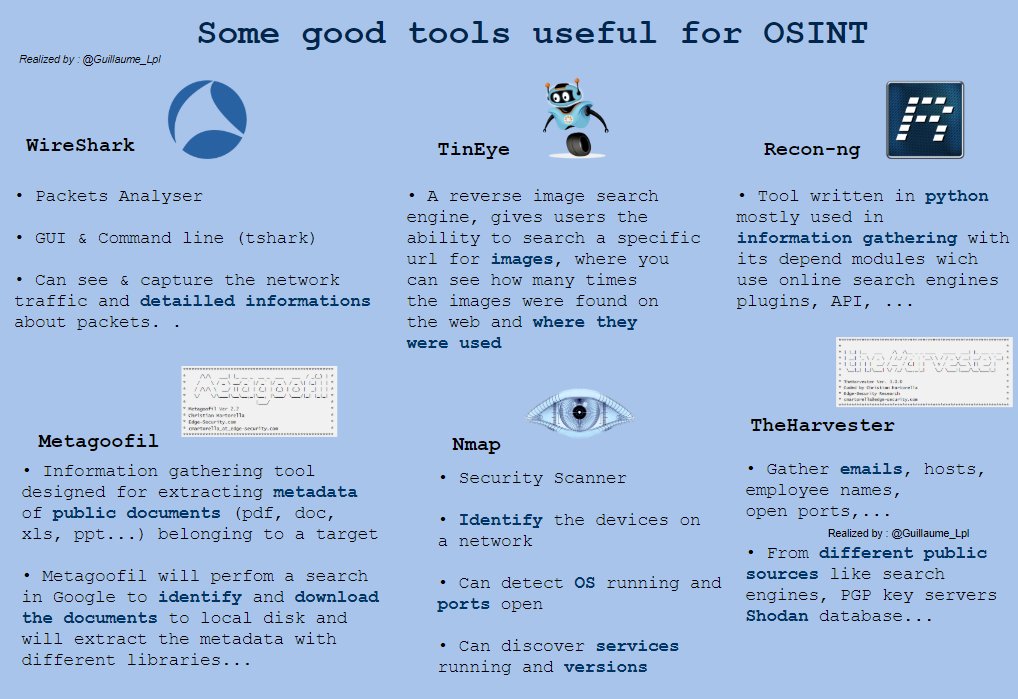
Tools for OSINT
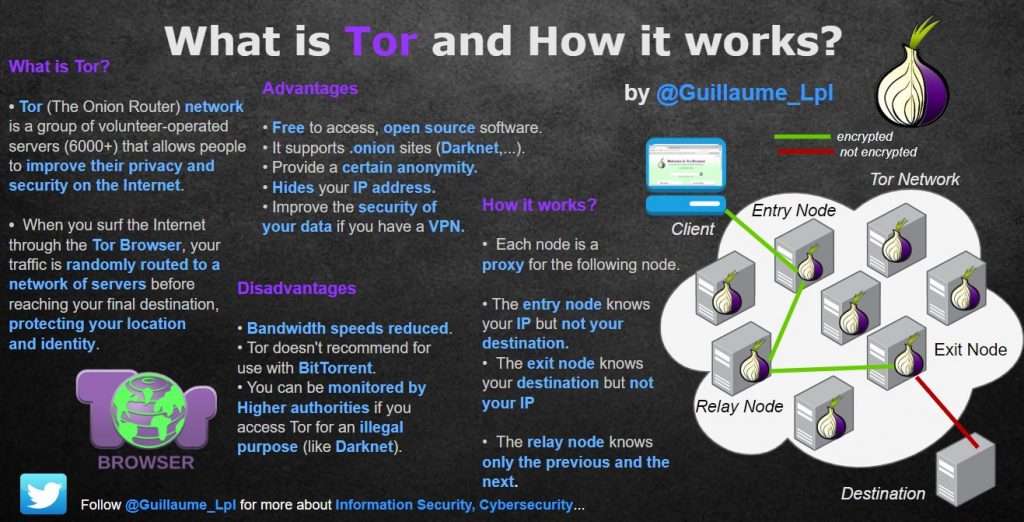
What is TOR and how it works
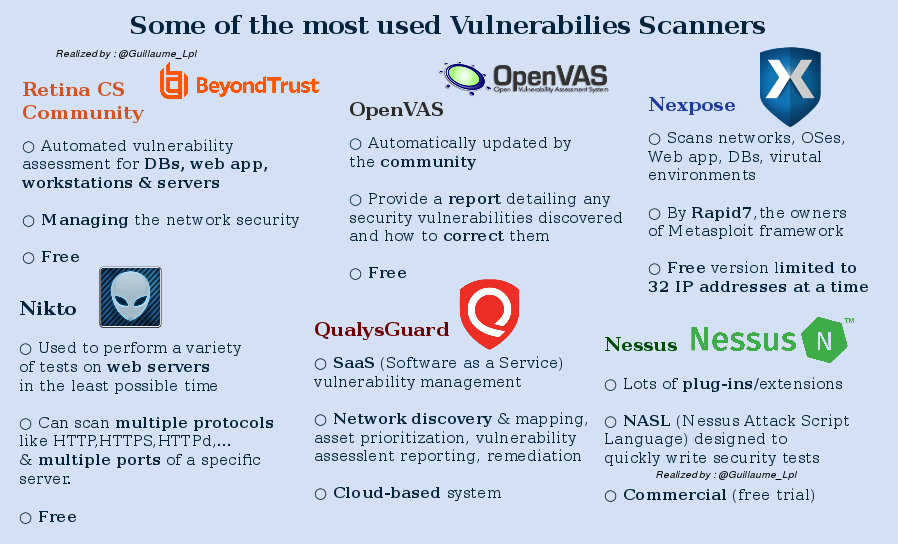
Vulnerability Scanners
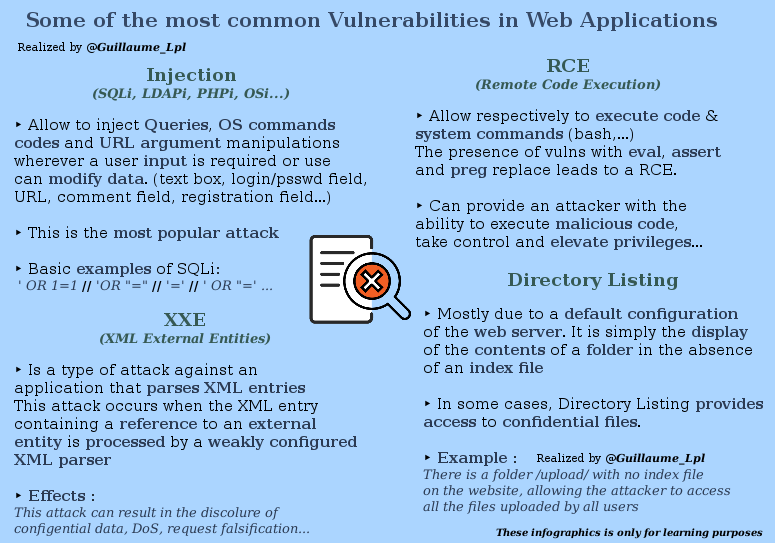
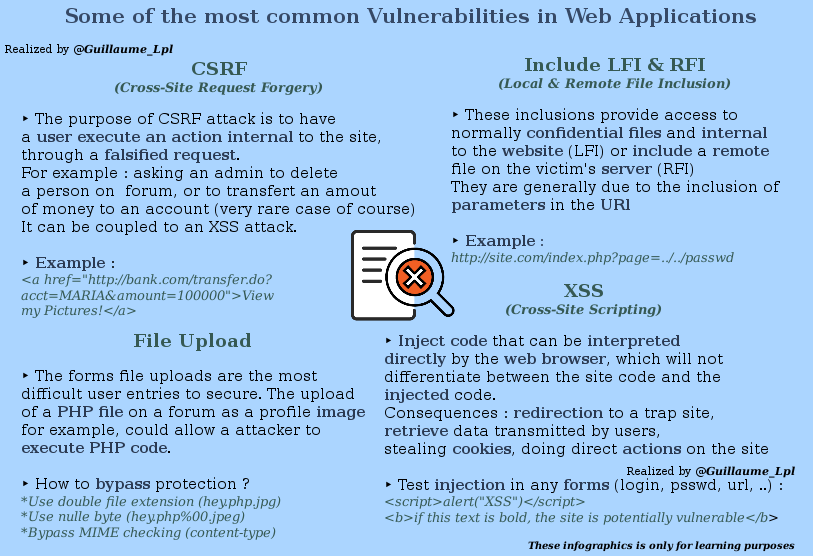
Most common vulnerabilities in web application
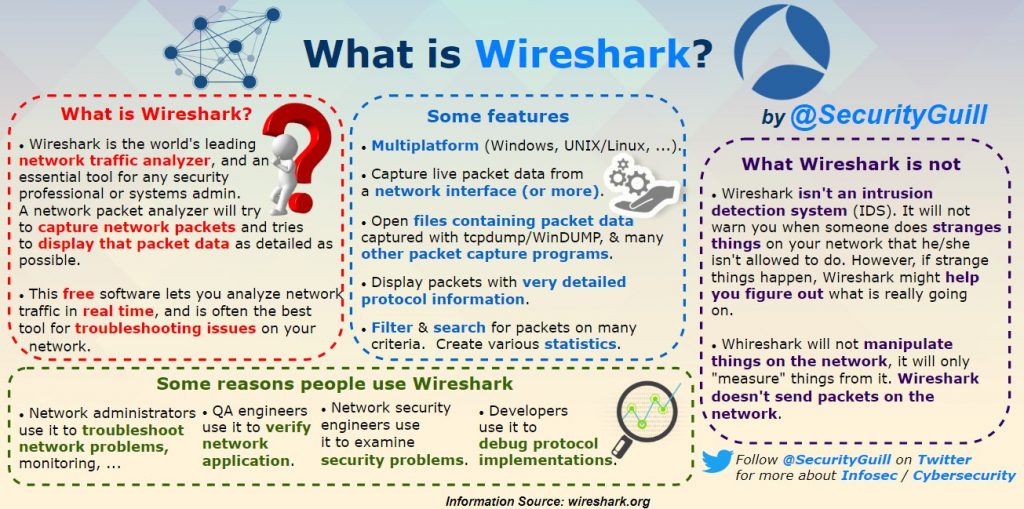
What is Wireshark?
What is XSS attack?

What is Zed Attack Proxy

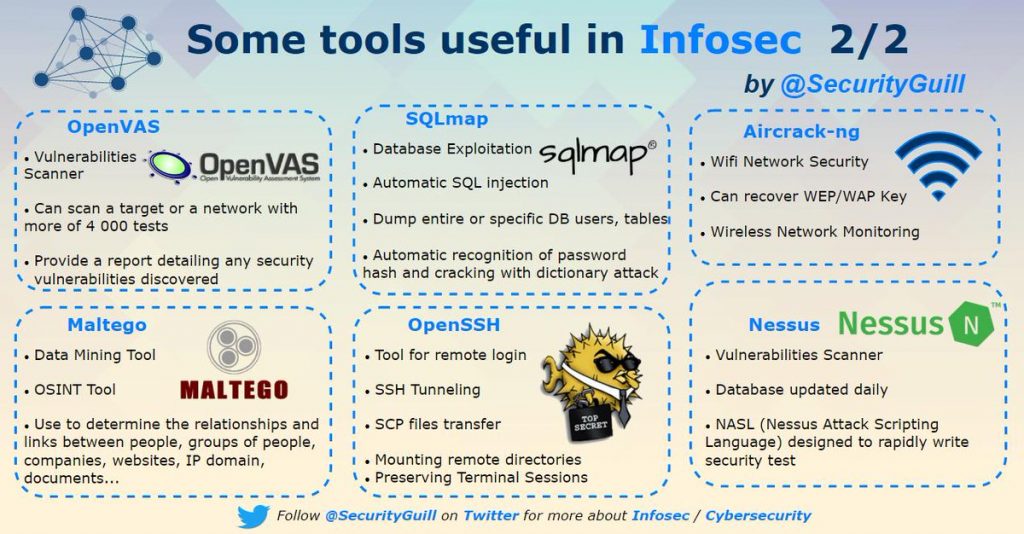
Infosec Tools